Granting the “Retrieve People Data for Search Crawlers” administration permission on the User Profile Service Application using PowerShell
When working with search-driven solutions, or even if you just want to be able to search for people, SharePoint Search has to be granted access to that information in order to crawl it. Generally all of this is being automatically taken care of when provisioning the Search Service Application. On rare occasions you might however need to grant this permission manually.
Granting the “Retrieve People Data for Search Crawlers” administration permission through the UI
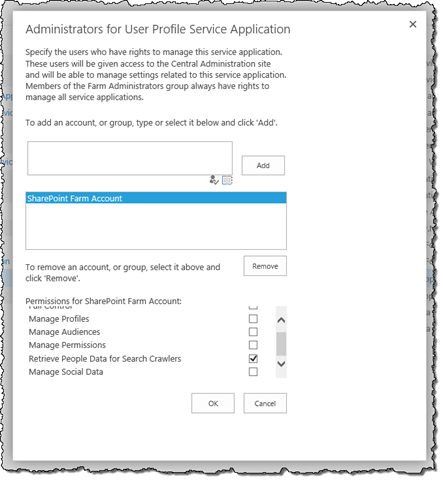
The “Retrieve People Data for Search Crawlers” administration permission can be configured through Central Administration by navigating to the Manage service applications page, selecting the instance of the User Profile Service Application and in the Ribbon clicking the Administrators button:
In the dialog window you can the select the account to which you want to grant the permission and the permission itself.
Granting the “Retrieve People Data for Search Crawlers” administration permission using PowerShell
Granting the “Retrieve People Data for Search Crawlers” permission through the UI is pretty straight-forward. Unfortunately there are organizations that don’t allow manual modifications to the Farm configuration and require scripts to perform any changes.
In the past I wrote an article on how you can grant permissions to the User Profile Service Application using PowerShell. Although granting administration permissions is very similar, there are some important differences between the two scripts.
Following is the PowerShell script that you can use to grant the “Retrieve People Data for Search Crawlers” permission to an account:
param (
$accountName
)
$claimType = "http://schemas.microsoft.com/sharepoint/2009/08/claims/userlogonname"
$claimValue = $accountName
$claim = New-Object Microsoft.SharePoint.Administration.Claims.SPClaim($claimType, $claimValue, "http://www.w3.org/2001/XMLSchema#string", [Microsoft.SharePoint.Administration.Claims.SPOriginalIssuers]::Format("Windows"))
$claim.ToEncodedString()
$upa = Get-SPServiceApplication | ? { $_.TypeName -eq 'User Profile Service Application' }
$accessControl = $upa.GetAdministrationAccessControl()
$rights = [Microsoft.SharePoint.Administration.AccessControl.SPCentralAdministrationRights](($accessControl.NamedAccessRights | ? { $_.Name -eq 'Retrieve People Data for Search Crawlers' }).Rights.GetHashCode())
$SPAclAccessRule = [Type]"Microsoft.SharePoint.Administration.AccessControl.SPAclAccessRule``1"
$specificSPAclAccessRule = $SPAclAccessRule.MakeGenericType([Type]"Microsoft.SharePoint.Administration.AccessControl.SPCentralAdministrationRights")
$ctor = $SpecificSPAclAccessRule.GetConstructor(@([Type]"Microsoft.SharePoint.Administration.Claims.SPClaim",[Type]"Microsoft.SharePoint.Administration.AccessControl.SPCentralAdministrationRights"))
$accessRule = $ctor.Invoke(@([Microsoft.SharePoint.Administration.Claims.SPClaim]$claim, $rights))
$accessControl.AddAccessRule($accessRule)
$upa.SetAdministrationAccessControl($accessControl)
$upa.Update()The biggest difference between the two scripts is that while previously we were able to directly specify the desired permission, in this case we have to retrieve it from the User Profile Service Application (lines 11 and 13). The reason for that is that the administration permission is a combination of other permissions and there is no type available in API to specify it directly.
Similarly to the previous script you can use the script above by passing the account name to which you want to grant the permission as the first parameter:
.\Set-UpaRetrievePeopleDataForSearchCrawlersPermission.ps1 "edge\administrator"Update 8/8/2014
It turns out that there is an easier way to grant the permission using PowerShell after all:
$upa = Get-SPServiceApplication | ? { $_.Name -eq 'User Profile Service Application' }
$security = Get-SPServiceApplicationSecurity $upa -Admin
$principal = New-SPClaimsPrincipal 'edge\administrator' -IdentityType WindowsSamAccountName
Grant-SPObjectSecurity $security $principal 'Retrieve People Data for Search Crawlers'
Set-SPServiceApplicationSecurity $upa -Admin $securityThanks to Jeffrey Schmitz (@DJeffa) for pointing it out.
Summary
In order for search to be able to crawl personal information, it needs to be granted access to that information. While in most scenarios this is automatically being taken care of, there are scenarios when you might need to configure it manually. The required permissions can be granted either through Central Administration UI or using PowerShell.