Help prevent data loss in Microsoft Flow with these 3 things
Now that your organization is using Microsoft Flow, are you sure that you set it up correctly so that it won’t leak your confidential information?
Automate what can be automated, but beware
If you don’t use Microsoft Flow in your organization, you should definitely give it a try. It will help you automate mundane tasks that are a part of your daily work and allow you to focus on where your attention truly makes a difference. Using the connectors and hundreds of templates made available by Microsoft, in a matter of minutes you will be able to automate processing e-mails, getting notified of changes or share information across your organization.
No matter if you’re an admin, developer, end-user or a business decision maker, you will be able to benefit of Microsoft Flow, because it doesn’t require any developer skills. But before you start using Microsoft Flow, you should double check if it’s configured correctly. The last thing you want, is to introduce another way to lose your organization’s data.
The power of Microsoft Flow
Using Microsoft Flow, you can connect multiple applications to automate your business processes in a matter of minutes. With the standard connectors, you can for example get notified, when new information arrives in Outlook, extract specific details and use it to create tasks, documents, notifications and instant messages. This is where Microsoft Flow truly shines: how it abstracts away the complexities of connecting multiple applications in a single flow allowing you to easily pass information from one application to another. And exactly because it’s so easy, you might forget where your organizational boundary ends and third party applications start. And that might be catastrophical for your organization’s information security.
Sharing data in Microsoft Flow
When you start building flows, you’re free to use the different connectors available in Microsoft Flow. Out of the box, you can connect to applications and services owned by Microsoft, such as Outlook, SharePoint or Azure Storage, but also to third party applications such as Twitter or Slack. And by default, there is no restriction which applications you can connect together. As a result, you can be almost certain, that your organizational information will leave your organization and be stored in third party services that your organization doesn’t govern.
So what can you do about it? Three things. At least, this is what you should start with.
Three things to configure in Microsoft Flow to help prevent data loss
Before you start using Microsoft Flow in your organization, there are three things that you should configure, as a first step towards keeping your confidential information inside your organization and the applications you govern.
Create data loss prevention policy
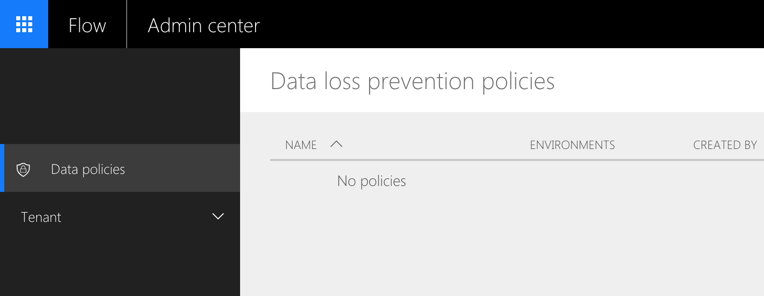
Data loss prevention policies allow you to control which applications have access to your organizational data. By default, you don’t have a data loss prevention policy for Microsoft Flow, which means there are no restrictions which applications users can connect to in their flows.
Before using Microsoft Flow in your organization, you should configure a data loss prevention policy. For more information how to do it, see the documentation at https://docs.microsoft.com/en-us/flow/prevent-data-loss.
Assign connectors to the right groups
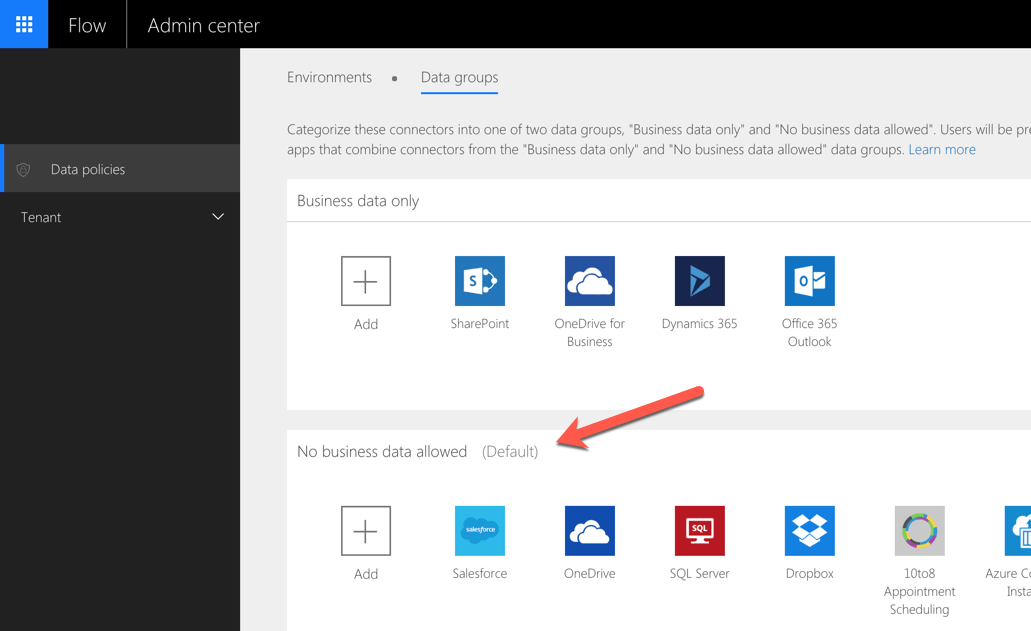
A part of creating a data loss prevention policy for Microsoft Flow, is assigning connectors to the two groups available in the policy: Business data only and No business data allowed. The labels are indicative and don’t impose any limitations by themselves, but they introduce an important boundary. Users are not allowed to use applications from different groups in the same flow..
For example, you might choose to put Outlook, SharePoint, OneDrive for Business and Planner in the Business data only group and Twitter, Trello and Slack in the No business data allowed group. As a result, users won’t be able for example to create a single flow with both the SharePoint and Twitter connector, helping you to ensure that organizational information won’t be shared on Twitter.
Correctly assigning connectors to the groups in a data loss prevention policy is something you should think through. Make it too restrictive, and Microsoft Flow will become useless. Allow everything, and you will be exposed to data loss. Unfortunately, there is no universal guidance for how to set it up. But you could for example start with moving applications that your organization uses and that are a part of Office 365 to the Business data only group and add more applications as your organization’s needs expand.
At the end of the day, it’s important that your organization accepts the risk of using the applications it put in the Business data only group, because these applications have access to your organizational data.
No business data allowed by default
When defining a data loss prevention policy for Microsoft Flow, you can choose which group is default: Business data only or No business data allowed.
At first the choice seems trivial. After all, you assign all applications to groups yourself. What you might not know though, is that every user in your organization is allowed to create a custom connector capable of connecting to external applications. When a connector gets created, it will be assigned to the default group in the data loss prevention policy.
At this moment, there is no validation or approval process for creating connectors and sharing them with others in your organization. Which is why, in order to prevent data loss, you want to ensure, that by default all connectors are assigned to the No business data allowed group. Only after they have been verified and approved by someone who has permissions to manage the data loss prevention policy for Microsoft Flow they would get access to organizational data.
Update Aug 5: After additional research it turns out, that custom connectors are assigned to the default data group in the data loss prevention policy. Unfortunately, at this moment, it’s not possible assign them to a different group. This however, should be possible in the future.
Summary
Microsoft Flow is a powerful asset to help users in your organization automate mundane tasks in their every day’s work. Left unmanaged however, it can lead to your organization losing sensitive data. Using the standard configuration capabilities of Microsoft Flow, you can take first steps to ensure that the data in your organization is not shared with applications your organization doesn’t govern.